The exercises included in this toolkit are intended to help users identify partners with whom they can establish useful collaborative relationships in order to address cybersecurity challenges in more effective and less costly ways. Understanding what those partnerships might be requires the user to be familiar with the types of cyber threats they face and the broad landscape of stakeholders interested in and potentially affected by attacks against their organization. The following exercise will provide users with a framework to synthesize this information and develop recommendations for taking action. The purpose is to encourage users to consider gaps in their existing cybersecurity methods and policies and to identify collaborative actions that will fill those gaps.
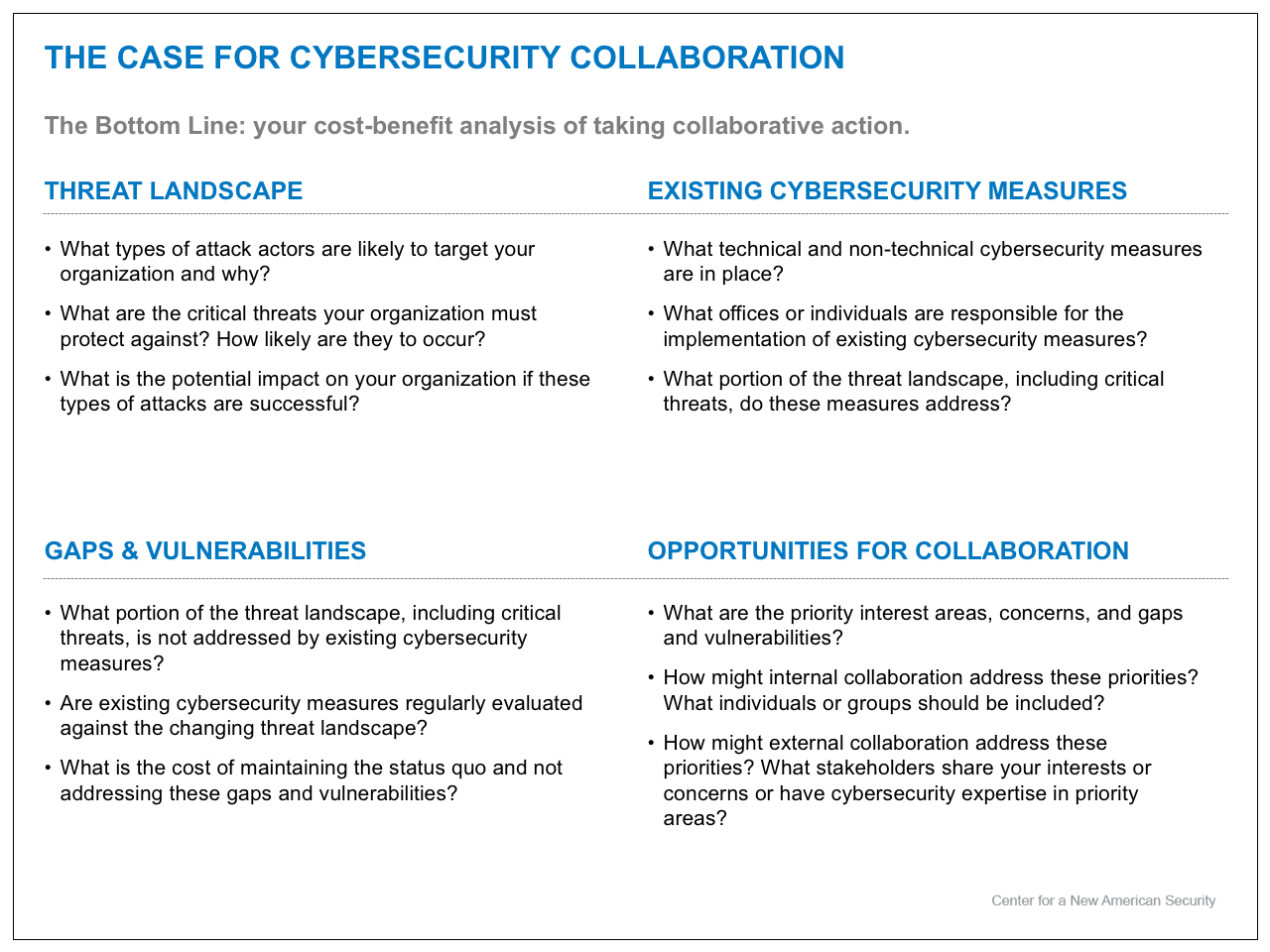
FRAMEWORK FOR ANALYSIS
Completing this framework will require you to draw from your analysis of the threat assessment and stakeholder identification and analysis exercises in addition to examining your organization’s existing cybersecurity measures.
Threat Landscape
The threat landscape encompasses the broad scope of cyber attacks that a particular organization or sector may experience in the near- to medium-term.
Describe your organization’s threat landscape:
- What types of attack actors are likely to target your organization and how capable are they?
- What assets are at risk and which could cause the most damage if compromised by a cyber attack?
- What are the critical threats your organization must defend against and why?
Existing Cybersecurity Measures
Existing cybersecurity measures include all technical and non-technical measures intended to prepare for, defend against, and respond to cyber attacks. These measures can include but are not limited to cyber hygiene, access controls, network security systems, membership in information sharing or support networks, and incident response plans.
Detail existing cybersecurity measures:
- What technical cybersecurity measures are in place?
- What non-technical cybersecurity measures are in place?
- What offices or individuals are responsible for the implementation of existing cybersecurity measures?
Gaps & Vulnerabilities
Gaps and vulnerabilities in cybersecurity can exist within an organization and between an organization and their key stakeholders. They are the result of a misalignment between existing cybersecurity measures, the threat landscape, and key stakeholders’ interests and concerns. Addressing such misalignment can help organizations minimize the risk of cyber attacks, adjust internal roles and responsibilities, and develop effective, comprehensive incident response plans.
Identify critical cybersecurity gaps and vulnerabilities:
- Do existing technical and non-technical cybersecurity measures address the current threat landscape, especially critical threats? Are there practical examples of successes or failures to address threats?
- Do existing technical and non-technical cybersecurity measures take into consideration the interests and concerns of key stakeholders? Are there practical examples of successes or failures to consider the interests of key stakeholders?
- Are existing cybersecurity measures regularly evaluated against the changing threat landscape and/or after the occurrence of a cyber attack?
Opportunities for Collaboration
Cybersecurity collaboration within areas of mutual interest or benefit can improve existing cybersecurity measures and address the gaps and vulnerabilities discussed above.
Determine priority areas for collaboration and potential partners:
- Which internal stakeholders are responsible for cybersecurity and addressing the impact of potential cyber attacks?
- What are our priority interest areas, concerns, and gaps and vulnerabilities?
- Which external stakeholders share these interests and concerns? How might collaboration with these stakeholders improve or lower the cost of cybersecurity measures while continuing to address the full threat landscape?
- Which stakeholders have expertise in areas where we identified gaps and vulnerabilities? Can partnerships be established to learn from their expertise?
Bottom Line
Cybersecurity is a field in which the offense will always hold an advantage; it is impossible to implement perfect defense all of the time. Therefore, it is essential to determine as many ways as possible to prepare for attacks and minimize the damage they cause. Effective communication and collaboration between relevant stakeholders improves situational awareness and establishes a stronger foundation for decision-making at a lower cost.
Assess the expected value from cybersecurity collaboration:
- What are the costs and/or benefits of maintaining the status quo?
- What are the costs and/or benefits of establishing internal and/or external collaborative relationships?
PRESENTATION SLIDE
The following slide provides a template that may be used to concisely organize and present the key points of analysis identified above to cybersecurity decision-makers in order to make the case for cyber collaboration.
Download Presentation Slide PPT Template